How to Get Legal, Procurement, and Business Units Onboard with Security
Legal, Procurement and business owners are often focused on their own objectives during the vendor onboarding and might not realize the necessity of having security in the room. With new, easy to sign up for and install tools, employees may engage a third-party without involving security teams at all or until the very end of the process. However, performing security assessments before contracting a new third-party is key to minimizing risk down the road.
Here are a few tips on how to get them aware and onboard with a security assessment.
What’s the role of security in the vendor onboarding and selection process?
The security team has the technical expertise to detect potential security threats around a new relationship. They need to have a good understanding of what systems, what level of access and data the vendor or third-party will have access to. They also need to ensure the third-party has the right precautions in place, such as system configurations or policies to ensure your data or your customers’ data is being handled properly.
According to new regulation, data mapping has become a major control in which companies need to ensure they understand where data resides and who it’s being shared with. Their expertise decides if there is enough confidence to engage in a relationship.
Therefore, it’s important that security gets ahead of any contract signing to make sure the third-party is taking the necessary steps to ensure data is secure. Areas like encryption, database configuration, patching cadences are for the experts to ensure are in place.
What happens if security is not involved upfront?
If the business owner or someone else from the company signs a contract before the security team has performed their review, they’re putting the company at risk.
They would be moving forward with a third-party who is going to have access to sensitive data without the necessary checks. If that third-party is breached and the sensitive data is leaked and it was something the Security team could have caught, that’s a huge risk for the company.
A Joint Vendor Onboarding Process
When legal, procurement and business owners join efforts and work together with security from the beginning, the process looks something like this:
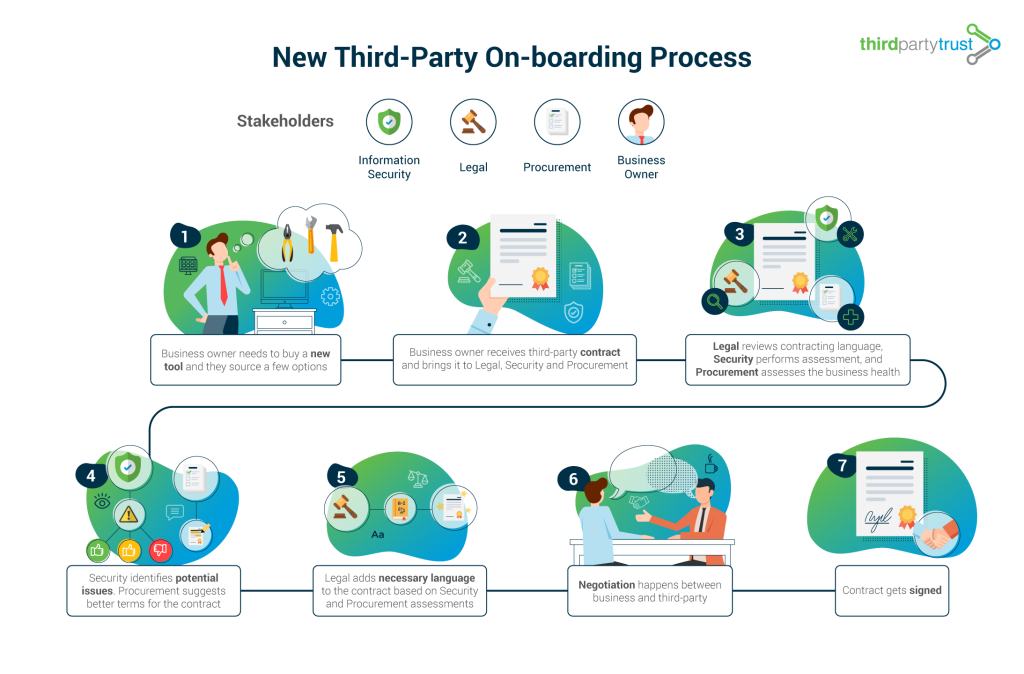
New Third-Party On-boarding Process
Stakeholders: Information Security, Legal, Procurement, Business Owner.
- Business owner needs to buy a new tool and they source a few options
- Business owner receives third-party contract and brings it to Legal, Security and Procurement.
- Legal reviews contracting language, Security performs assessment, and Procurement assesses the business health.
- Security identifies potential issues and approves, conditionally approves or denies the third-party. Procurement suggests better terms for the contract.
- Legal adds necessary language to the contract based on Security and Procurement assessments.
- Negotiation happens between business and third-party.
- Contract gets signed.
How to communicate the value of Security to each group?
Legal
Legal’s role in TPRM is to write language into the contract to make sure standards and controls are upheld through the life of the third-party relationship. This includes right to audit, compliance, business continuity, remediation and other contractual agreements that will protect the organization and prevent cyber, legal, financial and reputation risk.
Involving Legal is beneficial because they strive for greater efficiency, a line of sight into risks, and strong data control practices.
Tip: You should communicate to Legal that an inherent risk model will be used to assess the risk of the relationship, in order to provide a risk level that will the appropriate level of assurance. Resources will then be efficiently allocated to apply the appropriate level of scrutiny.
Procurement
Procurement focuses on getting key resources for the organization according to the business goals, and improving their quality and the terms around it. If the Business Owner is interested in a new TPRM tool, Procurement will help them get the best tool available according to the business-specific requirements.
Tip: Communicate to Procurement that the potential new TPRM tool will be a key resource to meet the business goals around cybersecurity and compliance.
Business Owner
The business owner is the one that detected a need within their team and wants to purchase a new tool to help with it. It’s in their best interest to ensure that product has the best security given the risk of the data being handled. If there’s an attempt to exfiltrate data from the third-party, the business owner wants to be assured they’ve taken the necessary precautions to protect their data.
Tip: Communicate to the business owner that the operational success of the new tool could be jeopardized, if it brings a new risk to the organization. All the more reason why they should include Security upfront in order to assess the new third-party.
To learn how our ThirdPartyTrust platform can help improve your TPRM strategy and vendor onboarding, request a demo now: