Third-Party Risk Management: The Good, the Bad, and the Ugly
Third-party risk management (TPRM) is the process of identifying, analyzing and mitigating risks associated with outsourcing to third-party vendors or service providers. There are many ways and frameworks to do it, but as we’ve come to understand from customer stories, organizations usually follow one of the following three: the good, the bad, and the ugly.
What we see most commonly is using spreadsheets and sending dozens of follow up emails, but that’s a thing of the past. We now have dedicated tools to assess and monitor third-party risk, which are lightyears ahead of traditional, heavy GRC tools.
It all comes down to how you approach the situation. As Blondie “The Good” said in the 1966 Western movie that inspired this blog:
“There are two kinds of people in the world. Those with guns and those that dig. You dig?”
Read on to discover what’s your TPRM type and how to do it the good way!
1. The Good: With a Focused Tool
The Good, the Bad, and the Ugly depicts Blondie as a confident bounty hunter and an expert at his craft. He exudes confidence as he knows there is nobody better at what he does.
Same thing happens to CISOs after they implement a focused tool for third-party risk management. They know they’ve made the right choice and they’re confident that they’ll reduce their workload while increasing capacity. Don’t just take our word: explore our case studies to discover why a focused tool is the way to go.
A perfect example of the good way is our own ThirdPartyTrust, a purpose-built TPRM workflow management, document repository and process automation platform. It automates and proceduralizes the most time consuming aspects of the traditional TPRM method (email and spreadsheets) so you can assess more third-parties with less internal resources.
Inversely, if you’re a third-party to someone else, you can scale your security response process by building a single repository for all questionnaires, certifications, and attestations, and share it with your customers with the click of a button.
Here go some reasons why ThirdPartyTrust gets chosen as a TPRM ally:
- Ease of use
- Easy implementation
- Light footprint in the network
- SSO and end-to-end encryption
- Unlimited Custom & Standard Questionnaires
- For third-parties, a single security profile to share with all customers
- For enterprises, a streamlined, automated process to assess third-parties
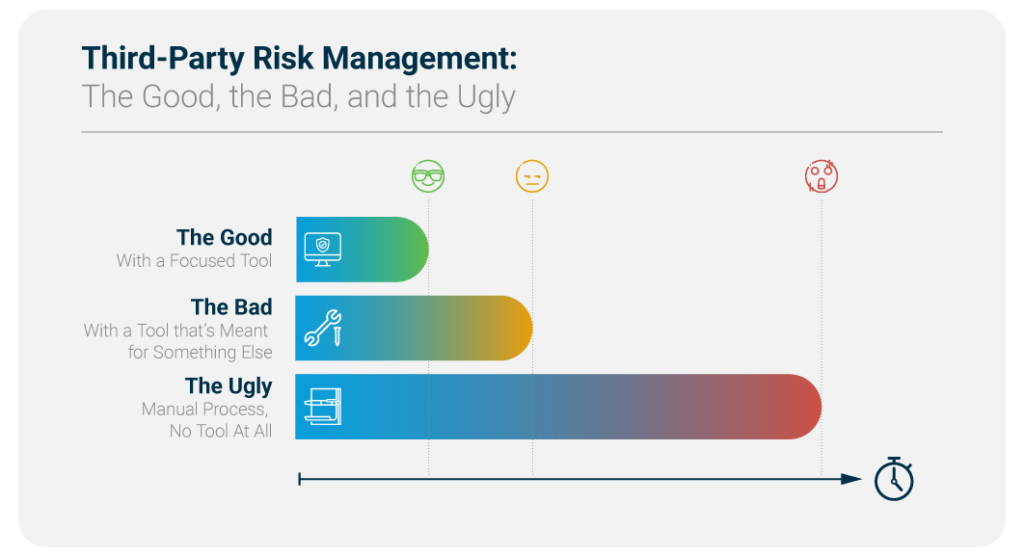
With a tool like this, the time needed to complete assessments is just a couple of hours, as you only need to invite your vendor or customer to the platform to share security documents and discuss any follow up questions. Your team can focus on analyzing data instead of collecting it.
Also, with automation built into the on-boarding and upkeep of vendor security documents, you can bring on hundreds of vendors in one year. Scaling your TPRM program with a risk-based approach was never this easy!
2. The Bad: With a Tool that’s Meant for Something Else
The Bad is a borderline-sadistic mercenary, which is not that different from trying to run an effective TPRM program on a GRC tool or supply chain platform. It’s almost as if the platform takes pleasure in killing your productivity… For the better of everyone, it’s time for the good to shoot the bad.
There are all sorts of tools that forcely added third-party risk management capabilities to their feature set. While their intentions are good, they’re tackling up functionality to an existing framework that may or may not work. For example, some GRC systems add features to track risks and questionnaires into a “magical” system, but they show some disadvantages:
- They’re too resource intensive
- There’s too much upkeep required
- Implementation can be hard and heavy
- There’s a very large footprint in the network
- They sometimes require in-premises installations as opposed to cloud delivery models
With a tool like this, the time needed to complete assessments can range from 1 to 3 days.
Also, organizations who complete 20 or more vendor assessments per month with multiple teams working at the same time can find it hard to suit their needs on a grand scale with these sorts of tools.
3. The Ugly: Manual Process, No Tool At All
As a supporting character, being comically oafish yet also cunning, cagey, resilient and resourceful can be great. But not so much when it comes to your TPRM program. Just as The Ugly, most people find themselves (figuratively) “at the end of the ropes.” Yes, he survived, but he curses his very existence and the situation he’s in.
Are you willing to suffer every time you need to complete an assessment? Or are you looking to make things smoother on both ends?
Most of our customers come to us tired of the manual TPRM process, which includes managing all due diligence and risk monitoring tasks via email. Obviously it’s very difficult to manage and takes a lot of time to process everything.

Furthermore, security documents are insecurely sent as attachments and there’s a lot of dependency of the analysts’ “gut feeling” to determine where the risks lie, as opposed to tools with continuous monitoring, data feeds, and automatic risk scoring.
With a process like this, the time needed to complete assessments can range from 3 to 15 days.
To Sum Up…
The key question to understand if it’s time to choose a dedicated TPRM tool is probably this: Given more resources, would you assess more vendors? If the answer is yes, then we’re here to help you automate and scale your program.
To learn more about how ThirdPartyTrust can help you streamline your TPRM program, request your free trial now:




