Google Fixes Zero Day Exploit In Chrome
Google Chrome was struck by a zero day attack for the fourth time in 2022, and Google is urging users to upgrade their browsers.
According to Google’s Project Zero blog, zero day exploits are increasing across all major platforms, and web browsers are no exception. If you use Chrome, make sure you update it.
About the vulnerability
As Forbes reported, the exploit (CVE-2022-2294) affects Windows and Android users and exists in the wild. Google also confirmed two other high-level security threats.
While details are restricted until users have had the chance to upgrade, the company has provided the following details about the vulnerabilities:
- CVE-2022-2294 [High]: Heap buffer overflow in WebRTC
- CVE-2022-2295 [High]: Type Confusion in V8
- CVE-2022-2296 [High]: Use after free in Chrome OS Shell
The first vulnerability affects WebRTC (Web Real-Time Communications), a technology that allows audio and video communication to work inside web pages via peer-to-peer communication, eliminating the need to install plugins or download native apps. In May 2010, Google bought GIPS, the company that had developed many components required for RTC, such as codecs and echo cancellation techniques. In 2011, Google launched WebRTC as an open-source project.
The second vulnerability affects V8, Chrome’s component responsible for processing JavaScript. Type confusion involves a lack of verification of the type of object that is received, and using it blindly without type-checking.
As for the third vulnerability, Use After Free, it relates to incorrect use of dynamic memory. After freeing a memory location, if the program does not clear the pointer to that memory, an attacker can use the error to compromise the program. This is one of the most common routes used to exploit the browser. In fact, almost 100 of these vulnerabilities have been found in Chrome in 2022 alone.
To fix these vulnerabilities, Google has released Chrome 103.0.5060.114 for Windows and 103.0.5060.71 for Android. While Android can automatically update and restart Chrome, Windows users need to do it manually.
The threat of zero days
Dealing with unpredictable zero day vulnerabilities is one of the greatest challenges faced by today’s security teams. According to the WatchGuard Internet Security Report, 67% of malware attacks used zero day exploits to succeed last year. Headline-grabbing cases such as SolarWinds and Log4j served as wake-up calls for many organizations.
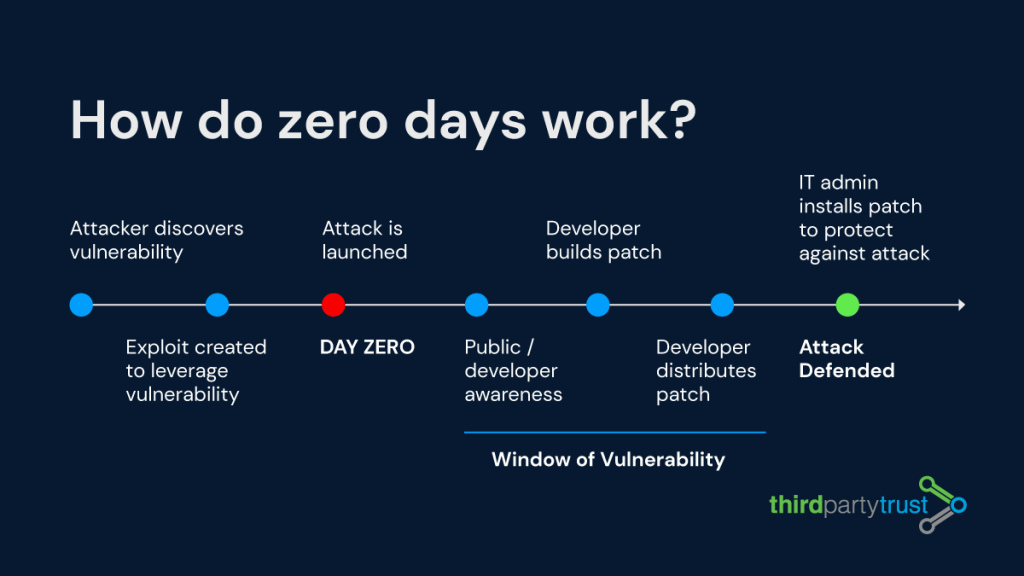
To help you stay ahead, we’ve compiled some resources and a quick guide: Everything to know about zero day attacks and remediation. We also have an on-demand webinar where you can get tips and tactics to reduce the risk of zero days.
Developers create software every day, but unbeknownst to them, it may contain vulnerabilities. This makes zero day attacks inevitable, as attackers often spot those vulnerabilities before the developers detect and act on them.
So how can you minimize risk in your organization?
Zero day protection measures include:
- Keeping all software and operating systems up to date, installing patches as soon as they become available.
- Enforcing security standards as part of your vendor risk assessments and updating your requirements if needed after a zero day is discovered.
- Performing continuous monitoring and reassessment of your vendors as opposed to point-in-time calendar evaluations.
- Using a layered defense strategy, combining antivirus, firewall, and other security solutions, with security mechanisms like zero trust or MFA.
- Educating users on cybersecurity best practices, especially amid flexible work arrangements; many zero day attacks capitalize on human error.
Let us show you how ThirdPartyTrust can help you reduce risk across your digital supply chain. Talk to an expert today.

Don’t let zero days be “wake up calls.”
Unpredictable vulnerabilities will be an ongoing concern for security teams inthe foreseeable future.
In this guide you will learn the fundamentals of zero days, patterns from our statistical analysis, and tips to reduce risk and remediate zero days if/when they happen.




