VRM and TPRM: What’s the difference?
As organizations engage with more third parties to scale their operations, risk and security leaders need to ensure that new and existing vendors are within their risk appetite. Yet 79% say their business is adopting technologies faster than they can address related security issues.
When trying to understand and reduce the inherent risk of dealing with vendors and third parties, vendor risk management (VRM) and third party risk management (TPRM) programs come to mind. What’s the difference between them, and which one do you need?
What is VRM?
Vendor Risk Management or VRM is the process of vetting new and existing vendors by performing risk assessments, in order to ensure that they do not create unacceptable potential for risk or business disruption.
Read more: What is Vendor Risk Management?
This includes any third party you regularly purchase from, from SaaS providers to manufacturers and more.
What is TPRM?
Third Party Risk Management or TPRM is the continuous process of identifying, analyzing, and controlling risks presented by third parties to an organization, its data, operations and finances. A TPRM program allows organizations to control the risk that arises from outsourcing services and products, by shedding light into areas of potential business risk.
TPRM is a broader discipline that covers VRM and other kinds of risk management, such as Supplier Risk Management or contract risk management.
Read more: What is Third Party Risk Management?
The difference between VRM and TPRM becomes even more clear when you think about vendors versus third parties.
Vendor vs. Third Party
While terms like supplier, provider, contractor, vendor, and third party are often used indistinctly, there’s a clear difference.
All vendors, suppliers, contractors, and providers are third parties to an organization, but not vice versa.
Third party is the overarching term to describe any organization that has a working relationship with another, including suppliers, contractors, providers, vendors, business partners, consultants, and more. It’s typically used as a catch-all term referring to a company that provides goods and services to your business, including business to business (B2B), business to customers (B2C), and business to government (B2G) business models.
Vendors are a type of third party that typically has a written contract with an organization and provides goods and services to them. The term “vendor” is most commonly used when referring to SaaS offerings, such as CRM, Payroll, or Marketing tools.
What’s the difference between VRM and TPRM?
As the names and definitions suggest, VRM focuses on vendors, while TPRM manages the risk of all kinds of third parties. TPRM expands the scope of a VRM program to include any outside party that could pose risk to the organization, including mergers and acquisitions, business partners, federal agencies, contractors, customers, and of course, vendors.
But the difference between VRM and TPRM is more than just a longer list of parties. In addition to completing a set of requirements to assess a third party’s security posture and make a decision, a TPRM program proposes a more holistic approach.
As organizations grow their third party ecosystem and accelerate their digital transformation, TPRM dives deeper to measure and continuously monitor third party security controls to align with your risk tolerance and organizational objectives.
Here’s how an end-to-end TPRM program looks like, where initial risk tiering, onboarding, and reassessment are typically part of a VRM program:
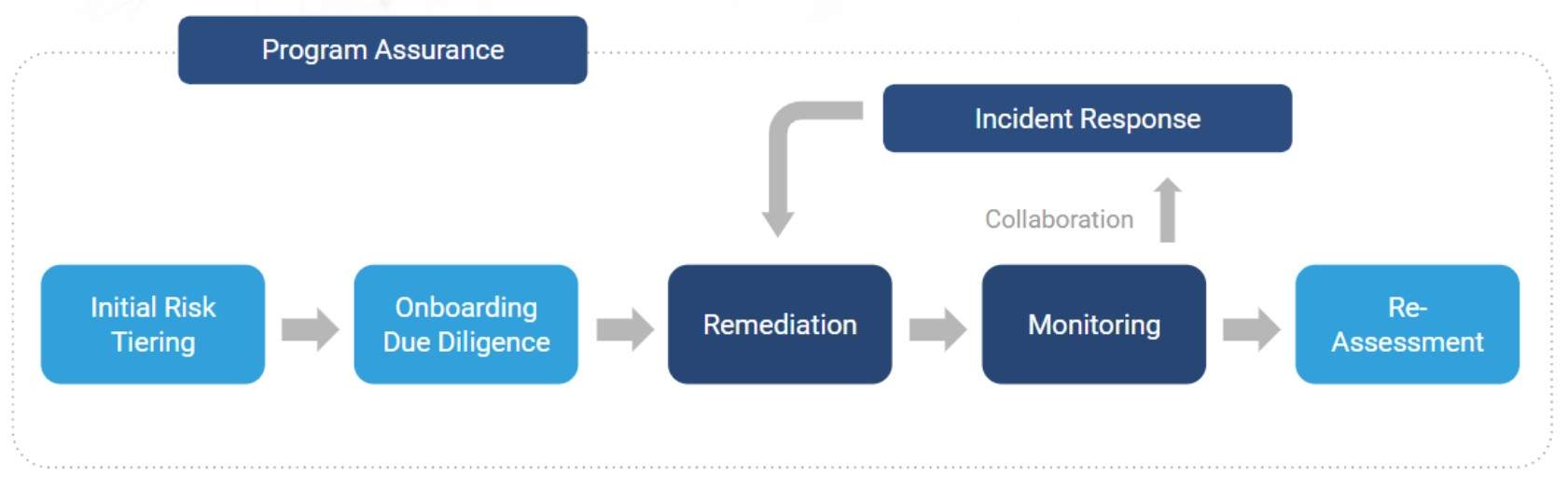
How does VRM fit into TPRM?
VRM can be considered a starting point for TPRM. It generally starts with a set of requirements to vet third party vendors and assess their security posture using a standard or custom information-gathering questionnaire, which helps to decide whether or not to engage with them.
Read more: How to conduct a vendor risk assessment
VRM covers everything from vendor selection, due diligence, procurement, onboarding, and offboarding, to ongoing monitoring and reassessment.
TPRM adds another layer of vendor validation, continuous monitoring, and effective assurance.
Do you need both VRM and TPRM?
The short answer is yes.
In most cases, it makes sense to start with a Vendor Risk Management program to develop a greater understanding of the inherent risk of your critical vendors; when it’s time to include other third parties, you will have a solid foundation to base it on.
Tools like BitSight VRM (formerly ThirdPartyTrust) make it easy to replace manual emails and spreadsheets with an automated workflow for vendor risk assessments, documentation exchange, and overall vendor management, including onboarding, reassessments, and offboarding.
But your digital supply chain includes many types of third parties that could cause a security incident, and keeping it safe goes beyond point-in-time risk assessments. Only a holistic approach to Third Party Risk Management will deliver solid evidence that your third parties’ security controls are being managed effectively.
How can we help?
With the acquisition of ThirdPartyTrust, BitSight delivers an end-to-end third party risk management solution that helps organizations:
- Assess and validate vendor security performance with confidence
- Continuously monitor third parties
- Effectively communicate risk to stakeholders
BitSight VRM can help you:
- Automate the risk assessment process to improve efficiency and stakeholder visibility while retiring manual tools like emails and spreadsheets.
- Prioritize critical and high-risk vendor assessments with customized workflows.
- Accelerate your efforts with insights from a network of 20,000+ vendor security profiles.
- Make better risk decisions with a process powered by BitSight’s best-in-class cybersecurity ratings and analytics.
BitSight TPRM can help you:
- Measure and continuously monitor third party security controls to align with your risk tolerance and organizational objectives.
- Effectively validate security controls across new and existing vendors.
- Continuously monitor controls to mitigate risk for third and fourth parties.
- Deliver evidence-based assurance to all stakeholders in order to drive confidence in your TPRM program.
Whether it’s getting started or taking your program to the next level, BitSight has the tools and services to help teams execute on their third party risk management programs.




