Risk Management Blog and Articles
January 14, 2021
Published by Sabrina Pagnotta on January 14, 2021
Categories
The journey towards full maturity will slow down as organizations adapt to the new normal. Here's how to face the TPRM challenges of 2021.
Do you like it?
January 7, 2021
Published by Sabrina Pagnotta on January 7, 2021
Categories
The landscape keeps shifting and organizations need to be looking ahead to new risks developing. Here’s how to train your foresight.
Do you like it?
December 30, 2020
Published by Sabrina Pagnotta on December 30, 2020
Categories
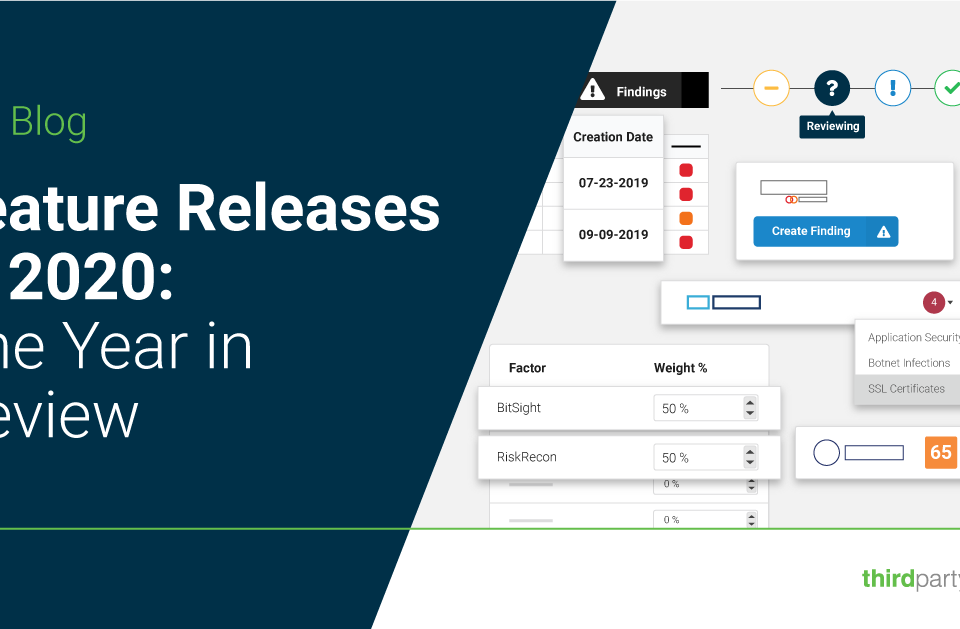
Despite the challenges 2020 posed, our platform continued to incorporate new features to make third-party risk management easier for enterprises and their vendors.
Do you like it?
December 21, 2020
Published by Sabrina Pagnotta on December 21, 2020
Categories
Pekin Insurance doubled the amount of vendors they can assess in the same time frame with a 3x ROI.
Do you like it?
December 17, 2020
Published by Sabrina Pagnotta on December 17, 2020
Categories
Data breaches caused by third-parties cost millions of dollars every year to large companies and are devastating to small businesses.
Do you like it?
December 15, 2020
Published by Sabrina Pagnotta on December 15, 2020
Categories
Vertafore built a simplified and digitized process to respond to security reviews, reducing the average time to completion to 24 hours.
Do you like it?
December 10, 2020
Published by Sabrina Pagnotta on December 10, 2020
Categories
The enemy is usually closer than we think or expect. Here's what James Bond can teach us about the importance of country.
Do you like it?
December 3, 2020
Published by Sabrina Pagnotta on December 3, 2020
Categories
What does it mean to innovate? We take some of James Bond's life lessons to achieve true security innovation.
Do you like it?
November 19, 2020
Published by Sabrina Pagnotta on November 19, 2020
Categories
Just like James Bond is in constant communication with M and the rest of HQ, so does a well functioning business.
Do you like it?